Close to 80% of companies have experienced cloud data breaches in the past 18 months. What are the leading causes of cloud risk—and how can businesses counter these challenges? Find out.
The cloud—with its ability to generate cost efficiencies and innovation—is critical to the growth of organisations. But to be able to leverage IaaS, PaaS and SaaS platforms, businesses need to be able to secure their cloud environments.
Unfortunately, in 2021, IDC unearthed that 90% of organisations had experienced at least one cloud data breach in the previous 18 months. And without the cloud, enterprises would be cut off from multiple benefits including improved cost-efficiency and cost-predictability, higher operational agility, enhanced resilience and customer experience, and data-driven business innovation and speed-to-market.
How do we know that security is essential to cloud adoption, and to accessing the cloud’s power? Primarily because the inverse is also true: Despite the fact that it’s been over a decade since enterprises started moving to the cloud, security is still the biggest barrier to adoption.
According to the Global Cloud Survey Report 2022, security, compliance, and governance are still the top hurdles to cloud adoption and success. “Though most organisations are engaged with cloud technology and have reached more mature phases in their cloud journeys, barriers remain. In fact, the barriers have remained fairly consistent, with Security, Compliance, and Governance still the top concern (identified by 72% of respondents), says the report.
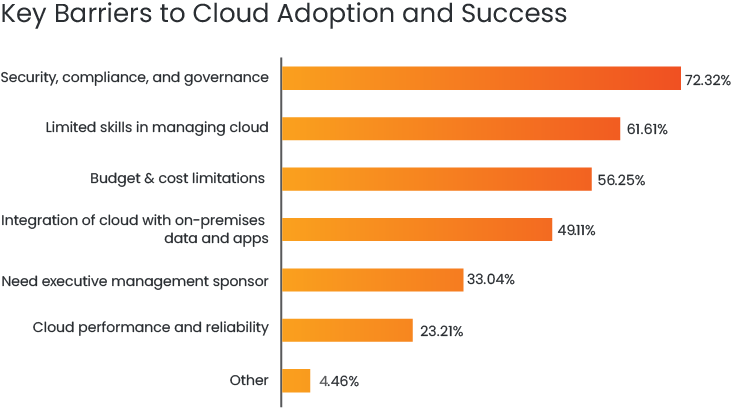
Source: Global Cloud Survey Report 2022
The State of the Cloud Report agrees. A full 85% of organisations say that security is their top cloud challenge—beating even significant stumbling blocks such as cloud migration and managing multi-cloud environments.
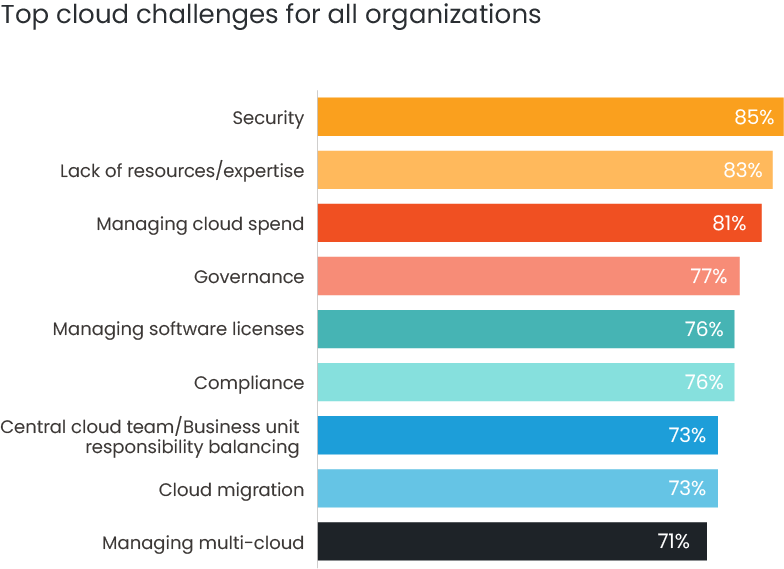
Source: State of the Cloud Report
Here’s the first answer to why it’s important to secure your cloud: Because without good cloud security, you stunt your business’ ability to leverage the cloud.
Organisations that can master cloud security, can also unleash the flywheel of innovation and growth that the cloud has to offer. Those that cannot? They risk financial and reputational losses at one end—and impair their ability to capture the future, on the other.
The Steep Price of Failure—and Leading Causes
The second important reason to effectively secure your cloud is simply this: Those that don’t pay a heavy price.
This toll can come in multiple forms including financial, reputational, data and IP losses. It also includes legal and regulatory action, downtime and a loss of productivity, and an erosion of customer and stakeholder trust, among others.
According to IBM’s Cost of a Data Breach Report, the average cost of a breach to a business is $3.86 million, and it takes 280 days to identify and contain it. While this figure covers breaches for workloads that are both in the cloud and on-premise, it’s instructive to note that 40% of businesses already run over 50% of their workloads in the cloud, points out the Cloud Security Report. And already 79% of companies have experienced at least one cloud data breach in the last 18 months, says Cloud Security Threats in 2022 report.
What’s worrying—in addition to the rise of ransom cloud attacks—is that 58% of business and security leaders expect an increase or a significant increase in attacks on cloud services in the future, says PwC’s 2022 Global Digital Trust Insights, and another 38% expect more serious attacks via the cloud in 2023.
A leading source of cloud security risk are misconfigurations. Over 60% of cybersecurity professionals report that misconfigurations are the biggest threat to cloud security, shows the Cloud Security Report. The Cloud Infrastructure Misconfiguration Survey Report, puts that number even higher: 92% of organisations are concerned about a major security breach due to misconfiguration. Regrettably, only 28% of companies continuously monitor for misconfigurations.
The Top 11 Security Threats in Cloud Environments: Cloud Security Alliance
- Insufficient Identity, Credentials, Access, and Key Management
- Insecure Interfaces and APIs
- Misconfiguration and Inadequate Change Control
- Lack of Cloud Security Architecture and Strategy
- Insecure Software Development
- Unsecured Third-Party Resources
- System Vulnerabilities
- Accidental Cloud Data Disclosure
- Misconfiguration and Exploitation of Serverless and Container Workloads
- Organised Crime/Hackers/APT
- Cloud Storage Data Exfiltration
Source: Cloud Security Alliance
Taking Back Control
There is a reason security continues to be the leading challenge organisations face as they create cloud foundations: It’s gotten a lot more complex.
What’s driving this complexity? A number of trends, which have come together to create a perfect storm of events. These include the growing popularity of hybrid multi-cloud environments, the continuing practice of remote working models, and the advent of modernisation with microservices and containers. IDC predicts that by 2024, 50% of organisations will use applications built on abstraction provided by cloud-native technologies.
Add to this the vulnerabilities that come with an increase in IoT endpoints, and the challenges associated with a rising number of partners and more complex supply chain attacks. Combined, these phenomena vastly increase the attack surface of businesses, while simultaneously shrinking the amount of visibility and control SecOps and DevSecOps teams have at their disposal.
The reality is that more distributed business and technology environments—including multi-clouds, microservices and containers—offer greater flexibility and an improved ability to innovate.
But they also create a by-product: Higher levels of vulnerability. In 2022, 75% of executives reported that there was too much complexity in their organisations, leading to concerning cyber and privacy risks, says PwC.
The result? Ineffective cloud security despite shared security models and powerful cloud security tools.
Here’s a case in point: According to a Cloud Security Alliance survey, a full 89% of companies say that the controls offered by their cloud service providers are effective—but businesses are not confident in their own ability to protect sensitive data in the cloud.
Most organisations report that their CSP security controls are highly effective (38%) or somewhat effective (51%). However, just under a third of organisations (31%) were not confident or only slightly confident about their ability to protect sensitive data in a cloud environment and another 44 percent reported they were only moderately confident
Compliance, too, is a large challenge. Over four in 10 (43%) of enterprises say that continuously staying in compliance, in dynamic cloud environments, is the most challenging cloud compliance process, points out the Cloud Security Report.
What is the way forward? First is achieving greater security visibility, and the ability to assess your organisation’s security posture more accurately across its multi-cloud estate. Over a quarter (26%) of companies say that cyber risk quantification is a critical capability for their current operating model, reports PwC.
Visibility empowers security leaders and teams to better gauge and prioritise risks, and align security action to business needs. Security leaders are aware of this, yet only one in five businesses assess their security posture in real time, according to the Cloud Security Threats report.
It is then crucial to adopt the capabilities to automatically detect, prioritise, and fix vulnerabilities, and automate compliance and security.
Ether offers a range of vulnerability management, cloud scanning, cloud compliance, and cloud security automation solutions that improve cloud security visibility and decision-making, lower the costs and the effort associated with cloud security, and enable you to surface challenges to better protect data, identities, access, applications, infrastructure, networks, and endpoints.
With Ether Cloud Security solutions, you will not only be able to secure hybrid, multi-cloud environments, you will also be able to capitalise on the potential of the cloud.
Learn more about Ether Cloud Security.



